IDENTIFY
Every strong cybersecurity strategy starts with understanding. In this phase, we focus on learning about the organization, its systems, data, and users. We identify what needs protection, where risks exist, and how potential threats could impact the business. This foundation allows us to make informed security decisions.
Asset & data discovery
Business and risk context
Threat & vulnerability analysis
Security priorities

STRATEGY
With a clear understanding of the environment, we define a tailored cybersecurity strategy. This step aligns security controls with business goals, ensuring protection without unnecessary complexity. We decide how to defend, where to focus, and which measures will deliver the most value.
Security architecture planning
Policies & standards
Risk-based control selection
Roadmap & governance

SECURE
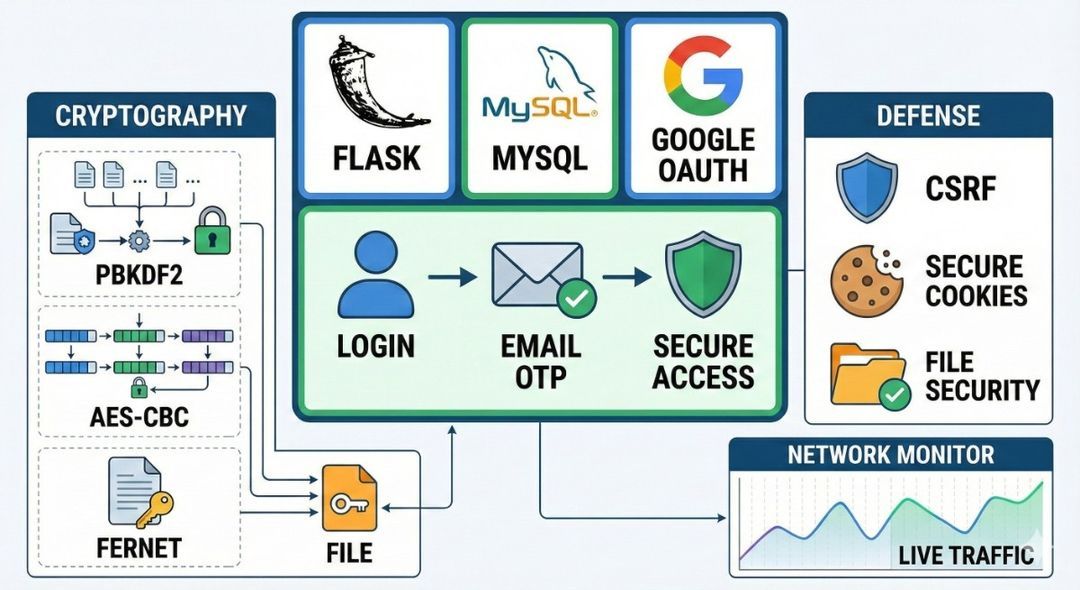
This is where the strategy becomes reality. We implement, monitor, and continuously improve security controls to protect systems and data. The goal is not only prevention, but also visibility and resilience—so threats are detected early and \led effectively.
Security control implementation
Monitoring & detection
Incident response readiness
Continuous improvement